FortiRecon - Threat Exposure Management
FortiRecon, a SaaS-based threat exposure management service, helps mitigate risk and manage exposures
Overview
What is FortiRecon?
FortiRecon is Fortinet’s AI and Human gathered intelligence-powered Continuous Threat Exposure Management service. A SaaS-based solution, it combines three robust modules—Attack Surface Management, Brand Protection, and Adversary Centric Intelligence, to provide security professionals with a complete view of all potential and imminent internal and external risks attackers can exploit.
Supply-Chain Vendor Risk Assessment
Continuously monitors vendor risks including attack surface exposure, ransomware incidents, leaked data
Identification & Mitigation of Brand Attacks
Alerts and takes down threats to your brand such as fake websites, mobile apps, social media accounts
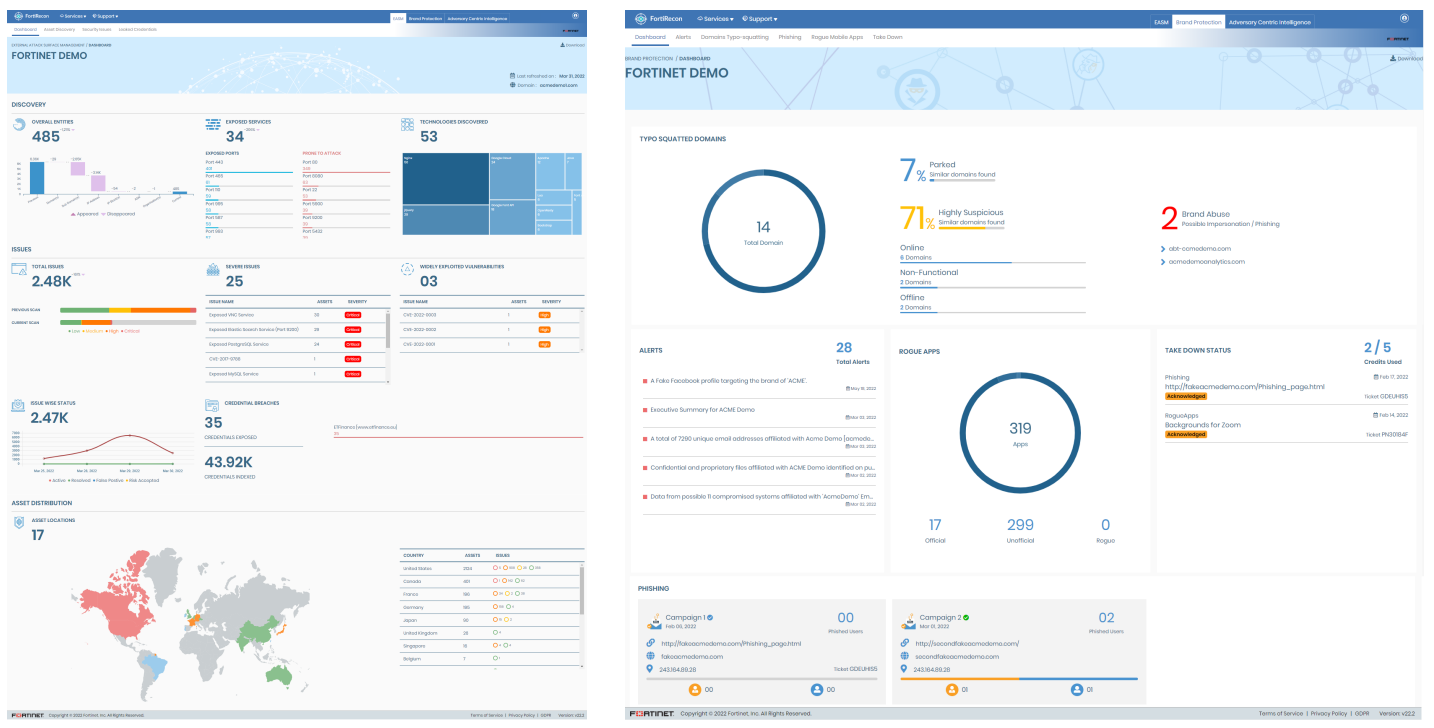
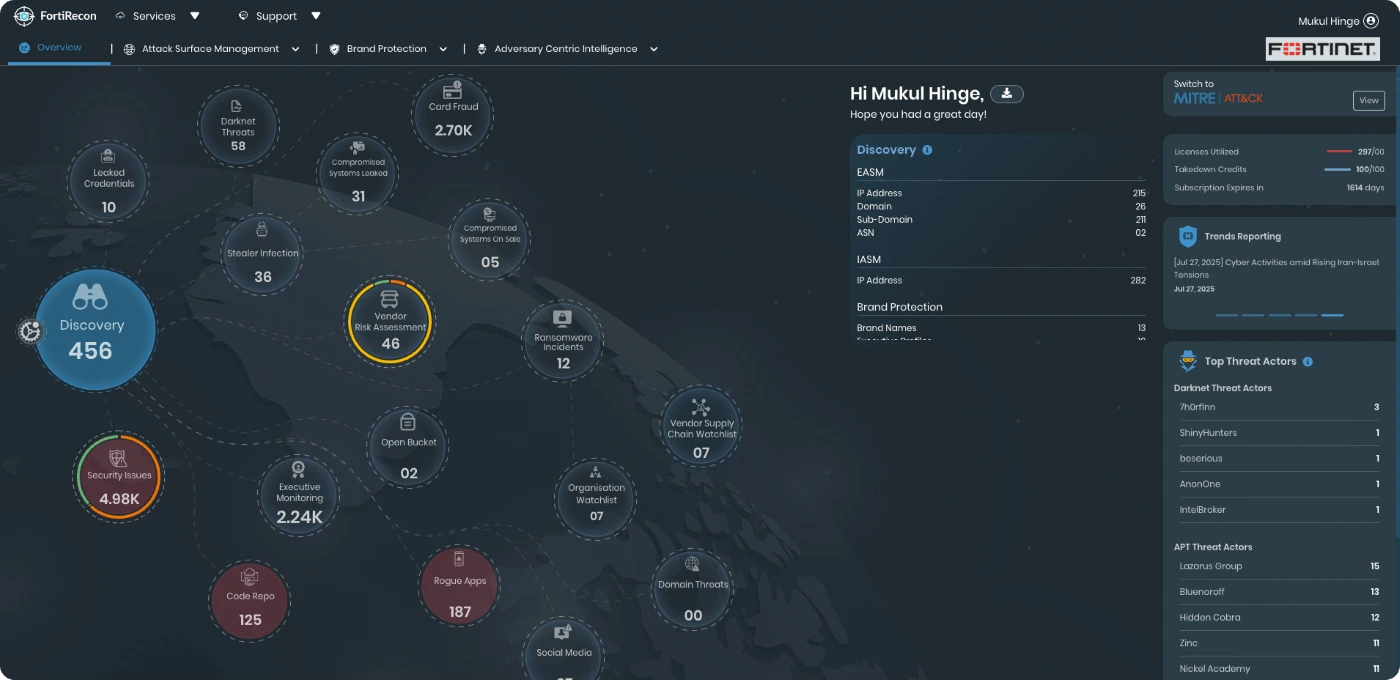
Continuous Internal & External Asset Discovery
Discovers and maps exposed assets that can be exploited by attackers
Security Orchestration
Integrates SIEM and SOAR for risk and threat intel correlation and orchestrated response
Takedown Services
Provides rapid response using FortiGuard Labs’ takedown services
Card-Fraud Monitoring
Provides info on credit/debit cards for sale on darknet marketplaces including breach info, images
Features
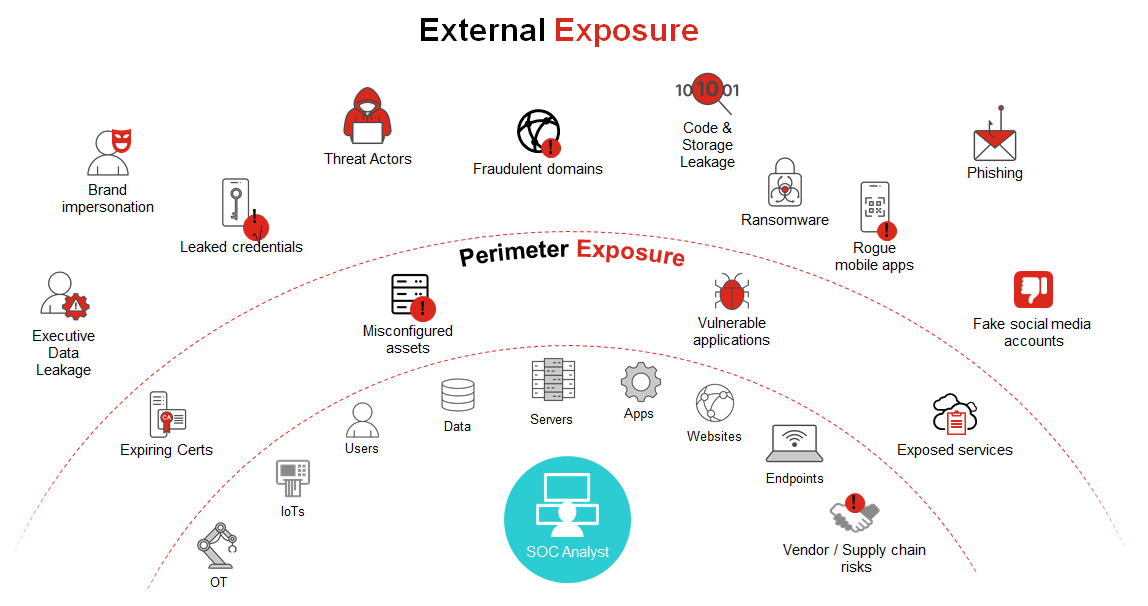
How FortiRecon Helps Streamline Your Continuous Exposure Management Program
FortiRecon helps prevent attacks even before they are launched, by
- Uncovering blind spots in your internal and external attack surfaces, from the viewpoint of an adversary, and providing detailed real-time insights into tactics, techniques, and procedures (TTPs) employed by threat actors
- Prioritizing the vulnerabilities that are at highest risk of exploitation and validating them with offensive tactics
- Combining disparate solutions into a single pane of glass that can be used to effectively orchestrate security
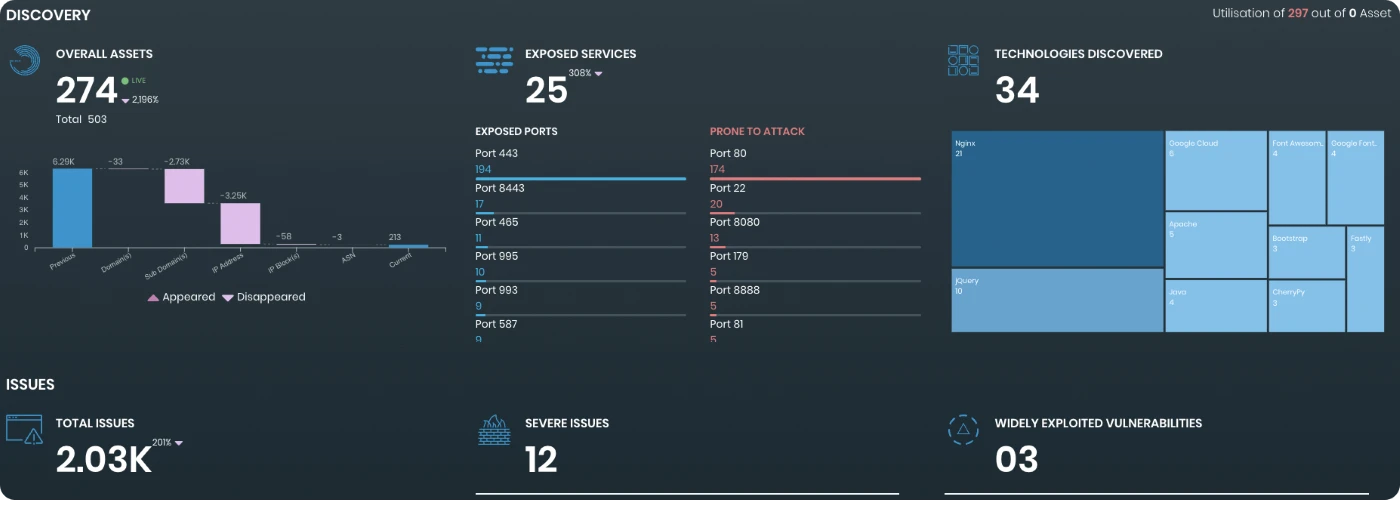
Attack Surface Management
The FortiRecon Attack Surface Management module continuously monitors and delivers an adversary’s view of the organization’s internal and external digital attack surfaces, and prioritizes risks and exposures. This enables security teams to proactively mitigate threats before they become an attack.
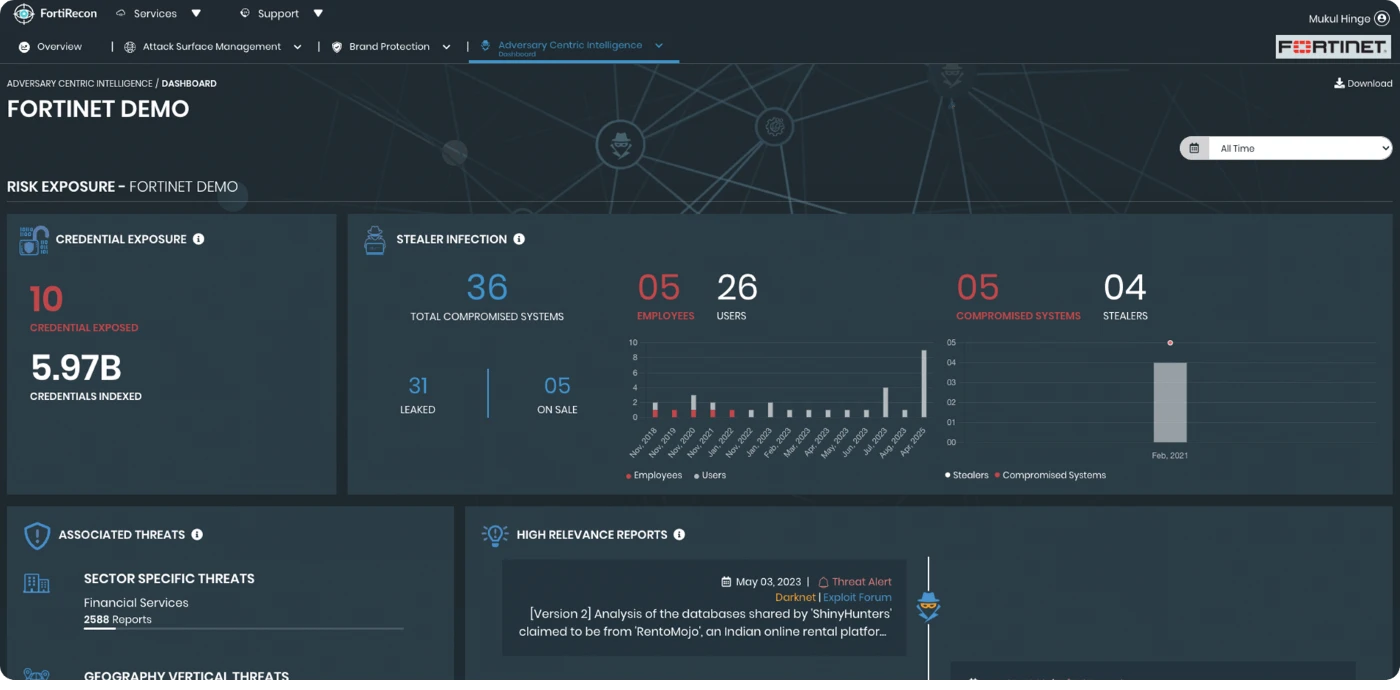
Adversary Centric Intelligence
The FortiRecon Adversary Centric Intelligence (ACI) module provides comprehensive coverage of dark web, open source, and technical threat intelligence. The intel includes ransomware intelligence, leaked credentials and card fraud, vulnerabilities being exploited in the wild, supply chain/vendor risk assessments, and threat actor insights. This helps security professionals proactively assess risks, respond faster to incidents, and increase the security awareness of their staff.
Brand Protection
FortiRecon Brand Protection uses proprietary algorithms to monitor, detect, and take down fake domains impersonating real ones. It also helps identify brand and executive impersonations, rogue mobile applications on multiple app stores, data leaks in code repositories, open bucket exposures, phishing campaigns, and helps protect executive online presence.
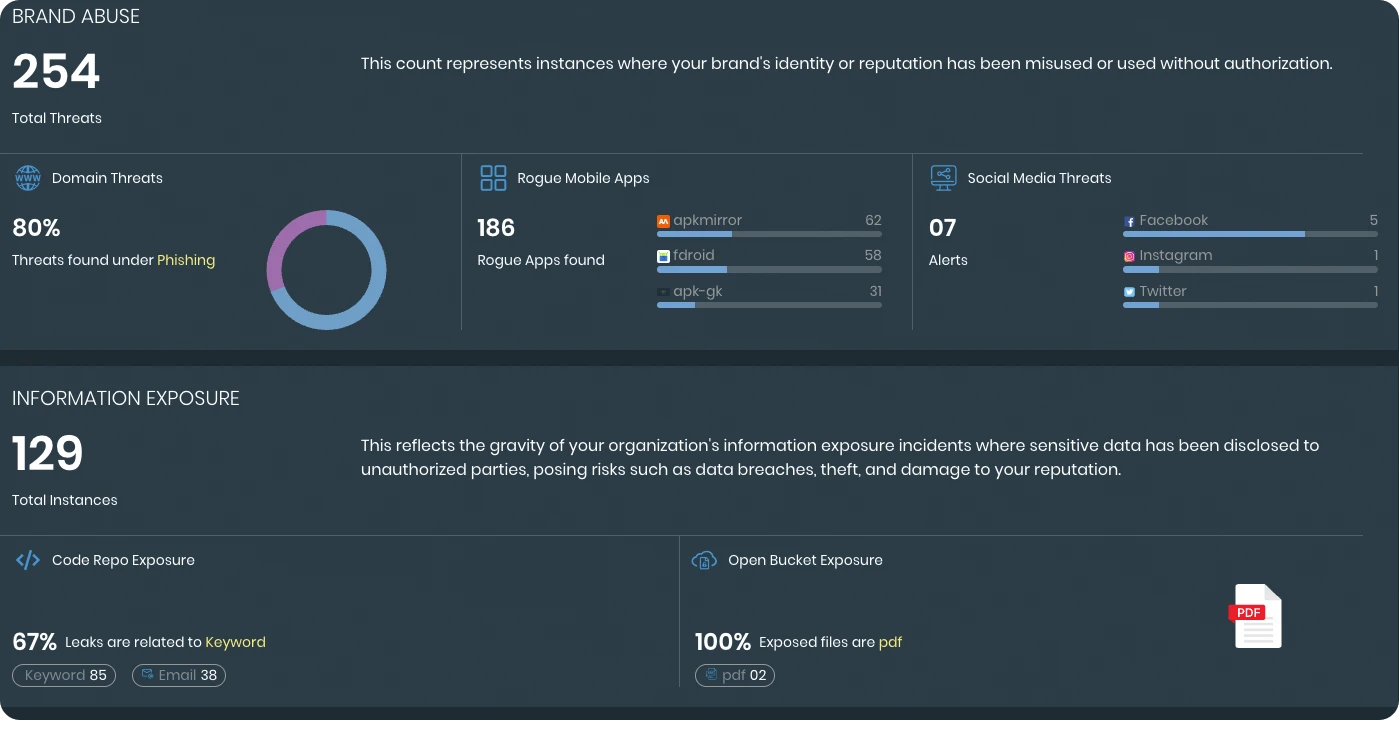
FortiRecon Use Cases
Vulnerability Intelligence and Prioritization
Monitor and report on vulnerabilities and exploits being actively used and discussed on the dark web.
Ransomware Intelligence
Monitor ransomware threat actors’ activities and report on relevant past and potential targets and TTPs.
Security Orchestration and workflow automation
Automate and streamline security workflows with inbuilt and custom playbooks.
Actionable Threat Insights
Get early warning on risks to your brand, enterprise assets, supply chain vendors, and software.
Attack Surface Monitoring: MITRE ATT&CK View
Map detections to MITRE ATT&CK framework, get an accurate picture of the TTPs attackers can use or are currently using against you.
Identify domain, social, and phishing threats
Detect and take down rogue domains and mobile applications, monitor executive threats, card fraud, code repo, and open bucket exposures.