Fortinet FortiClient
FortiClient is a Fabric Agent that delivers protection, compliance, and secure access in a single, modular lightweight client. A Fabric Agent is a bit of endpoint software that runs on an endpoint, such as a laptop or mobile device, that communicates with the Fortinet Security Fabric to provide information, visibility, and control to that device. It also enables secure, remote connectivity to the Security Fabric.
FortiClient Product Details
FortiClient can be purchased with three levels of capability: Zero Trust Security, Endpoint Security, and Cloud-based Endpoint Security.
FortiClient 7.0
FortiClient’s Fortinet Security Fabric integration provides endpoint visibility through telemetry and ensures that all Security Fabric components – FortiGate, FortiAnalyzer, EMS, managed APs, managed Switches, and FortiSandbox – have a unified view of endpoints in order to provide tracking and awareness, compliance enforcement, and reporting. Traditional virtual private network (VPN) tunnels or new, automatic ZTNA tunnels provide secure remote connectivity. Provide security and protection for endpoints when local or remote.
- Unified Endpoint features including compliance, protection, and secure access into a single modular lightweight client.
- Universal ZTNA, with automatic, encrypted tunnels for controlled validated per-session access to applications.
- Advanced Threat Protection against exploits and advanced malware, powered by FortiGuard along with FortiSandbox integration.
- Simplified Management and Policy Enforcement with FortiClient EMS, FortiClient Cloud, and FortiGate.
Central Management Tools
- Simple and user-friendly UI
- Remote FortiClient deployment
- Real-time dashboard
- Software inventory
management
- Active Directory (AD)
integration
- Central quarantine
management
- Automatic group assignment
- Dynamic access control
- Automatic email alerts
- Supports custom groups
- Remote triggers
- On-premise and cloud-based
options
FortiClient Unifies Endpoint Features
FortiClient is a Fabric Agent that delivers protection, compliance, and secure access in a single, modular lightweight client. A Fabric Agent is a bit of endpoint software that runs on an endpoint, such as a laptop or mobile device, that communicates with the Fortinet Security Fabric to provide information, visibility, and control to that device. It also enables secure, remote connectivity to the Security Fabric.
The FortiClient Fabric Agent can:
- Report to the Security Fabric on the status of a device, including applications running and firmware version.
- Enable the device to connect securely to the Security Fabric over either VPN (SSL or IPsec) or ZTNA tunnels, both encrypted. The connection to the Security Fabric can either be a FortiGate Next-generation Firewall or SASE service.
- Send any suspicious files to a Fabric Sandbox.
- Enforce application control, USB control, URL filtering, and firmware upgrade policies.
- Apply CASB controls to users accessing cloud-based applications.
- Provide malware protection and application firewall service.
Features & Benefits

ZTNA
Delivers better REMOTE ACCESS and consistent application access policies

FABRIC AGENT
Provides telemetry information and leverages integrations to the rest of the Fortinet SECURITY FABRIC

WEB FILTERING
Provides web security and CONTENT FILTERING

SOFTWARE INVENTORY MANAGEMENT
Enables visibility and license management

CASB
Control access to cloud-based applications, including visibility to shadow IT

AUTOMATED RESPONSE
Detects and isolates compromised endpoints
Bundles:
| FORTICLIENT EDITION |
VPN / ZTNA |
EPP / APT |
MANAGED SERVICES |
| Zero Trust Network Access (ZTNA) |
|
|
|
| Central Management using FortiClient Cloud |
|
|
|
| Central Logging and Reporting |
|
|
|
| SSL VPN with MFA |
|
|
|
| IPsec VPN with MFA |
|
|
|
| SSO Mobillity Agent |
|
|
|
| CASB (Inline and API) |
|
|
|
| Vulnerability Agent and Remediation |
|
|
|
| FortiGuard Web Filtering |
|
|
|
| USB Device Control |
|
|
|
| FortiSandbox (On Premise or PaaS) |
|
|
|
| FortiClient Cloud Sandbox |
|
|
|
| AI-powered NGAV |
|
|
|
| Automated Endpoint Quarantine |
|
|
|
| Ransomware Protection |
|
|
|
| Endpoint Onboarding |
|
|
|
| Initial Provisioning |
|
|
|
| Security Fabric Setup/Integrationg |
|
|
|
| Vulnerability Monitoring |
|
|
|
| Endpoint Security Monitoring |
|
|
|
| Best Practice Service (BPS) Consultation |
Account add-on |
Account add-on |
N/A |
| Forensic Analysis Service (FAS) |
Account add-on |
Account add-on |
Account add-on |
| 24x7 Support |
|
|
|
| On-Premise/Air Gap Option |
|
|
|
Services:
FortiClient Managed Services
To assist and offload busy IT teams, Fortinet is offering
FortiClient Managed services to streamline the configuration,
deployment, and monitoring of FortiClient agents. Services
included with this offering include the following.
- Initial FortiClient Cloud provisioning: The managed
services team works with customers to set up and
configure their FortiClient Cloud environment for the
following capabilities
- Endpoint groups setup
- ZTNA
- VPN
- Endpoint security
- Vulnerability management
- Security profiles and policies configuration
- Endpoint posture check rules
- Custom FortiClient installer creation and ongoing
installer updates
- Endpoint onboarding: The managed services team
creates customer FortiClient installers for customerspecific use cases, sends invitation emails to users, and
onboards them for FortiClient Cloud management and
provisioning.
- Security Fabric setup and integration: The managed
services team integrates FortiClient Cloud with the
Fortinet Security Fabric to support uses cases such as
ZTNA, incidence response, and automation.
- Endpoint vulnerability monitoring: The managed
services team monitors customer endpoints to identify
high risk endpoints and alert them of endpoints with
critical and high vulnerabilities that would be easy targets
for cyber attacks. The managed services team detects,
reports, and guides customers to remediate those
vulnerable endpoints.
Best Practice Service (BPS)
FortiClient Best Practices Service is an account-based annual
subscription providing access to a specialized team that
delivers remote guidance on deployment, upgrades, and
operations. The service allows customers to share information
about their deployment, user requirements, resources, and
other related items. Based on the information provided,
the BPS experts can provide recommended best practices,
sample code, links to tools, and other materials or assistance
to speed adoption and guide the customer towards best
practice deployments. The team does not log into customer
devices to make changes for them. This is a consulting and
guidance service which may include sample configurations or
playbooks. This is not an on-site professional services offer.
FortiClient Forensics Analysis Service
FortiClient Forensic Service provides analysis to help endpoint
customers respond to and recover from cyber incidents.
For each engagement, forensic analysts from Fortinet’s
FortiGuard Labs will assist in the collection, examination, and
presentation of digital evidence, including a final, detailed
report. FortiClient subscriptions that include Forensic
Services entitle the customer to call on these endpoint
forensic experts whenever an event happens, offloading
internal teams and accelerating investigations by analysts
deeply familiar with the tools of endpoint security. Forensics
Analysis Service is only available for cloud-hosted EMS
deployments.
Fortinet CASB Service
To safely embrace the cloud, a Cloud Access Security Broker
(CASB) can act as a gatekeeper by providing visibility, control,
and protection to allow organizations to extend their security
policies beyond their own infrastructure. CASB sits between
cloud service users and cloud applications, monitors all
activity, and enforces security policies. Fortinet’s dual mode
solution provides security, scalability, and performance using
both Inline and API-based CASB protections to address all
cloud security needs. A FortiClient license enables Inline
CASB services on a FortiGate and provides a license for
FortiCASB, Fortinet’s API-based CASB service.
Feature Highlights:
Software Inventory Management
provides visibility into
installed software applications and license management to
improve security hygiene. You can use inventory information
to detect and remove unnecessary or outdated applications
that might have vulnerabilities to reduce your attack surface.
Windows AD Integration
helps sync organizations’ AD
structure into the central management tools so that you
use the same organizational units from your AD server for
simplified endpoint management.
Real-time Endpoint Status
always provides current
information on endpoint activity and security events.
Vulnerability Dashboard
helps manage organizations attack
surface. All vulnerable endpoints are easily identified for
administrative action.
Centralized FortiClient Deployment and Provisioning
that
allows administrators to remotely deploy endpoint software
and perform controlled upgrades. Makes deploying FortiClient
configuration to thousands of clients an effortless task with a
click of a button.
FortiSandbox integrations
assist with configuration and
suspicious file analysis. Sandbox settings are synchronized
across managed endpoints, simplifying setup. A detailed
analysis of FortiClient submitted files is available in the central
management tools. Administrators can see all the behavior
activity of a file, including graphic visualization of the full
process tree.
Telemetry
provides real-time endpoint visibility (including
user avatar) on FortiGate console so administrators can get
a comprehensive view of the whole network. Telemetry also
ensures that all fabric components have a unified view of the
endpoints.
Dynamic Access Control for Compliance Enforcement
requires EMS to create virtual groups based on endpoint
security posture. These virtual groups are then retrieved
by FortiGate and used in firewall policy for dynamic access
control. Dynamic groups help automate and simplify
compliance to security policies.
Endpoint Quarantine
helps to quickly disconnect a
compromised endpoint from the network and stop it from
infecting other assets.
Automated Response
helps detect and isolate suspicious or
compromised endpoints without manual intervention.
Application-based Split Tunnel
supports source applicationbased split tunnel, where you can specify application traffic to
exclude from the VPN tunnel, such as high bandwidth apps.
Web Filtering with Keyword Search / YouTube Filters
blocks
web pages containing words or patterns that you specify
as well as limit users’ access by blocking or only allowing
specified YouTube channels.
Software Specifications:
| |
Windows |
MAC OS |
Android |
iOS |
Chromebook |
Linux |
| Endpoint Telemetry |
|
|
|
|
|
|
| Compliance Enforcement Using Dynamic Access Control |
|
|
|
|
|
|
| Endpoint Audit and Remediation with
Vulnerability Scanning |
|
|
|
|
|
|
| Remote Logging and Reporting |
|
|
|
|
|
|
| IPSec VPN |
|
|
|
|
|
|
| SSL VPN |
|
|
|
|
|
|
| ZTNA Remote Accesss |
|
|
|
|
|
|
| Windows AD SSO Agent |
|
|
|
|
|
|
| USB Device Control |
|
|
|
|
|
|
| Antivirus |
|
|
|
|
|
|
| Cloud-based Threat Detection |
|
|
|
|
|
|
| Sandbox (on-prem) |
|
|
|
|
|
|
| Sandbox (cloud-based) |
|
|
|
|
|
|
| Automated Endpoint Quarantine |
|
|
|
|
|
|
| Web Filter |
|
|
|
|
|
|
| AntiExploit |
|
|
|
|
|
|
| Application Firewall |
|
|
|
|
|
|
Use Cases:
FortiClient is more than just an advanced endpoint protection solution with a built-in VPN client. It connects the endpoint with the Security Fabric and delivers integrated endpoint and network security. With the modular design, users can deploy FortiClient for some or all of the use cases.
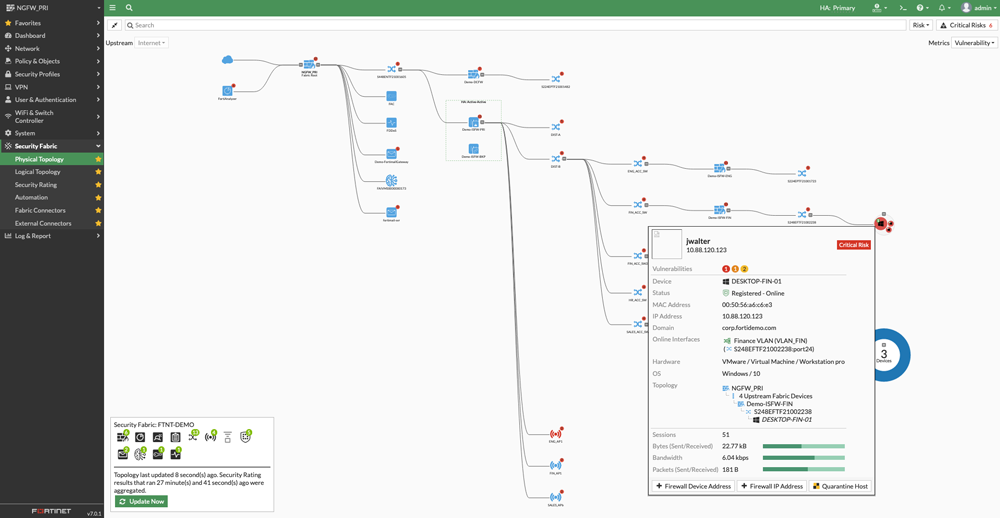
Security Fabric Integration
Endpoint Visibility and Compliance Control
FortiClient ensures endpoint visibility and compliance throughout the Security Fabric and integrates endpoint and network security with automation and segmentation. FortiClient shares endpoint telemetry with the Security Fabric, enabling unified endpoint awareness.
In addition, it is also compatible with third-party anti-malware or endpoint detection and response (EDR) solutions.
Secure Remote Access (VPN, ZTNA)
Ensure secure remote access with always-on, SSL/IPsec VPN that supports network segmentation, conditional admission, and integrates with FortiAuthenticator for single sign on, and multi-factor authentication.
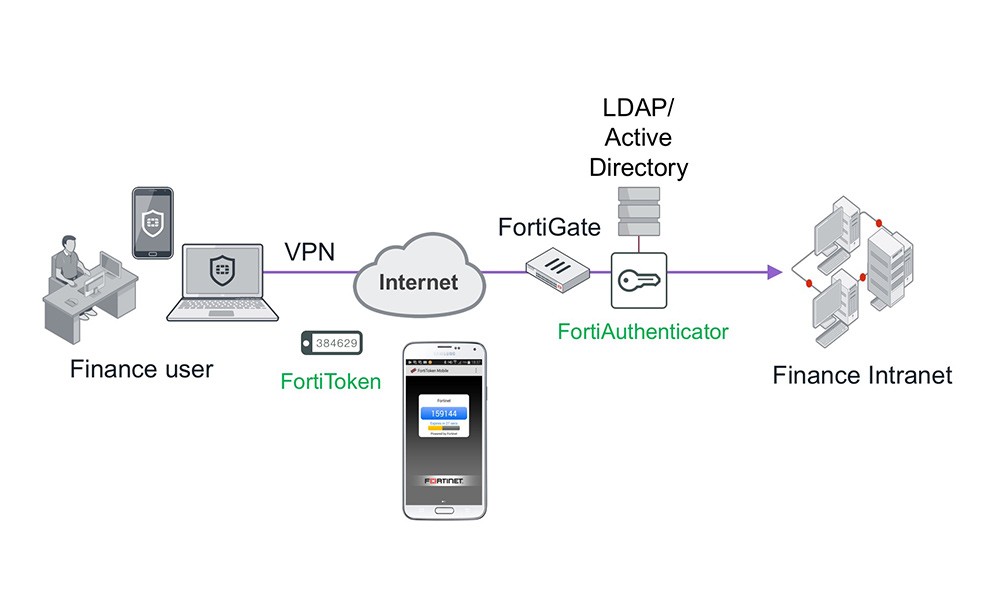 Traditional VPN
Traditional VPN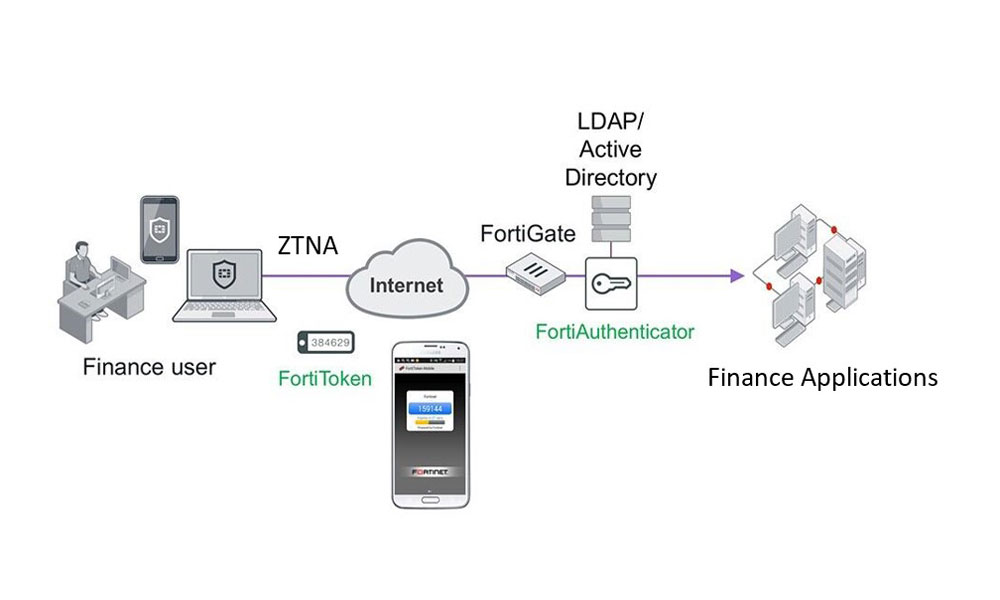 ZTNA Application Access
ZTNA Application Access
Endpoint Hardening
99% of the vulnerabilities exploited continue to be ones known by security and IT at the time of the incident. FortiClient enables vulnerability scanning with automated patching, software inventory, and application firewall to help reduce the attack surface and boost overall security hygiene.
As part of the telemetry shared throughout the Security Fabric, endpoint vulnerability information allows network security operations teams to take additional measures, such as dynamic access control, to help secure the environment.
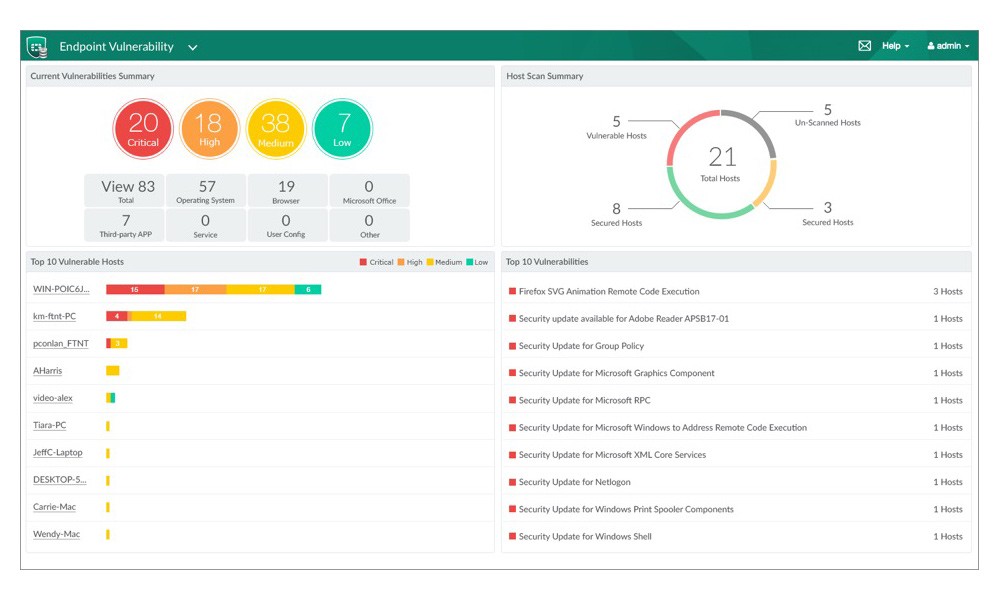
The FortiClient vulnerability dashboard delivers detailed information including category, severity, and can pinpoint the affected endpoints.
Advanced Endpoint Protection
Secure endpoints with machine learning antimalware and behavioral-based anti-exploit. Sandbox integrations detect advanced threats, customer malware, and script-based, file-less attacks. Application firewall, intrusion prevention system (IPS), botnet protection, and web content filtering provides additional layers of protection.
FortiClient also natively integrates with FortiSandbox. It can block the execution of any never-before seen file and automatically submit them to the sandbox for real-time analysis. Real-time threat intelligence from FortiSandbox is instantly shared across the enterprise to all endpoints.
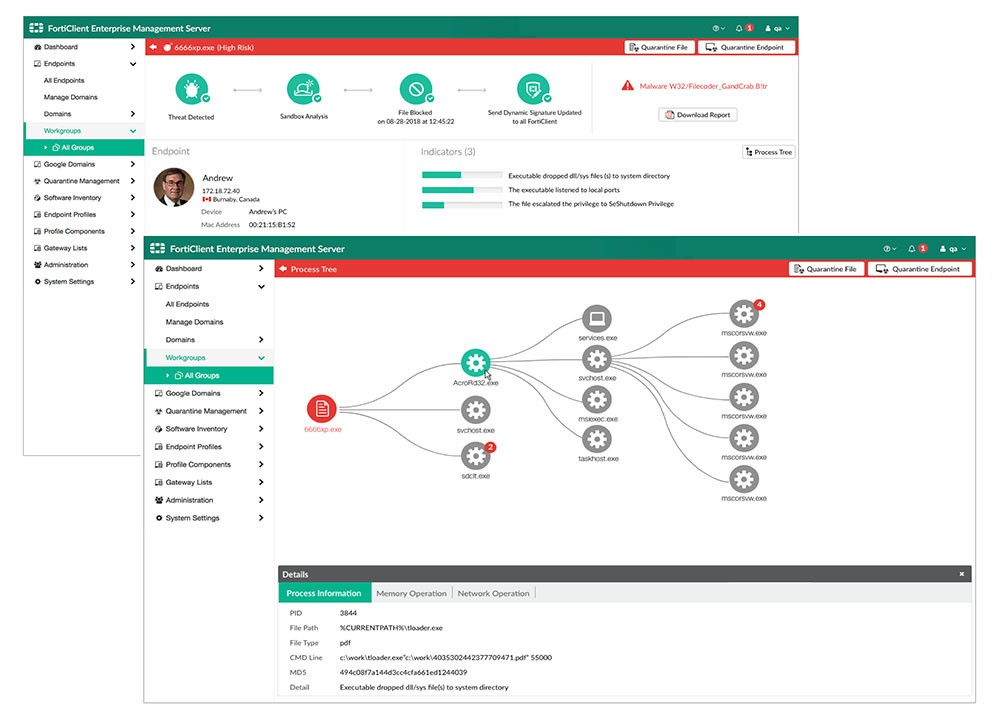
The FortiClient endpoint management console shows detailed analysis from FortiSandbox.