Lacework-CNAP-Kubernetes-Security

Overview:
Comprehensive Kubernetes Security
- Harden K8s security posture, find vulnerabilities, and automatically detect unusual behavior and runtime threats without writing rules.
Secure K8s early in software lifecycle
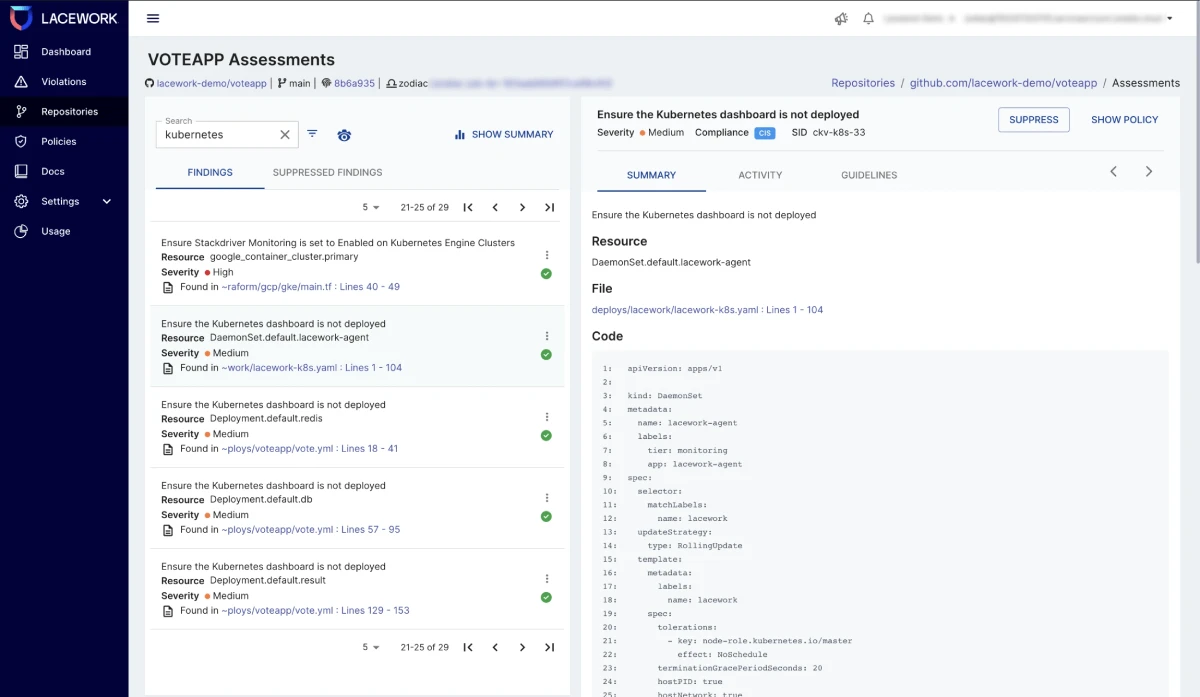
- Rapidly find and fix vulnerabilities and misconfigurations within Kubernetes Manifest, Helm, Terraform, and more.
- Automate security and compliance guardrails at each commit and pull request within GitHub and GitLab repositories.
- Boost developer productivity with actionable findings and guided remediation tightly integrated within existing toolchains and workflows.
- Dramatically reduce cloud risk by preventing non-compliant and misconfigured Infrastructure as Code from being deployed.
Focus on image risks that matter most
- Incorporate Composite Alert technology to correlate risk factors and combine build and runtime insights.
- Automatically detect or block non-compliant container images through the Kubernetes Admission Controller before deployment.
- Perform fast on-demand scans of container images or schedule every 15 minutes using auto-polling.
- Continuously scan new and existing images within public and private registries.
Harden K8s security posture (KSPM)
- Automatically discover all Kubernetes assets and resources including workloads, pods, nodes, and more.
- Enforce least privilege, protect secrets, ensure containers are not running as root, and harden KSPM security posture.
- Quickly assess compliance with CIS, HIPAA, ISO, NIST, PCI, SOC 2, and other regulations.
- Track assets for 90 days and monitor how workloads, RBAC, and resource configurations drift over time.
Detect threats in Kubernetes runtime
- Continuously monitor node, container, and K8s runtime activity to detect malicious behavior like container escape or lateral movement.
- Understand how clusters, namespaces, and containers communicate with cloud services, domains, and other resources.
- Visualize network activity, processes, user behavior, and topology with Polygraph® technology.
- Leverage Composite Alerts that combine signals to detect unusual activity, unknown threats, and zero-day exploits.
Know exactly who is doing what in K8s
- Continuously collect and analyze massive volumes of K8s API calls to gain visibility into user and resource activity.
- Automatically detect user activity, RBAC issues, deleted resources, authentication errors, forbidden API calls, and more.
- Visualize and trace API calls between IP addresses, K8s and AWS groups, usernames, and target resources.
- Query Polygraph intelligently with filters like actions, namespace, and resource names to focus on specific activity paths.
Features:
Highly Dynamic and Configurable K8s Cause Security Issues
- The dynamic nature of Kubernetes creates complexity and blind spots for security and compliance. Secure K8s with comprehensive visibility.
- Rules alone can’t protect against unknown threats in K8s environments. Automate detection without writing complex rules.
- Hundreds or thousands of alerts overwhelm security teams. Composite Alerts accelerate response time and provide meaningful insights with context.
Run Kubernetes with Confidence
- Automate guardrails at every stage of the cloud-native application lifecycle and prevent misconfigured K8s resources from being deployed.
- Take advantage of composite alert technology from FortiCNAPP to comprehensively scan your Kubernetes clusters.
- Empower developers and DevOps teams to secure applications effortlessly within existing workflows and avoid last-minute delays.
- Gain visibility into unusual behavior and previously unknown or zero-day threats within Kubernetes and running container workloads.