Lacework-CNAP-SBOM
Enterprise-Grade Protection for Smaller Networks
Overview:
Know More, Develop Faster
Equip developers with more code security risk context without disrupting workflows.
Prioritize and fix your biggest risks
- Identify vulnerabilities tied to your code dependencies.
- Find and prioritize third-party and open-source vulnerabilities with application context filtering (ACF).
- Accelerate remediation with auto-generated pull requests for updating each vulnerable package.
- Track ownership by knowing which developer is responsible, the status of each fix, and who needs support.
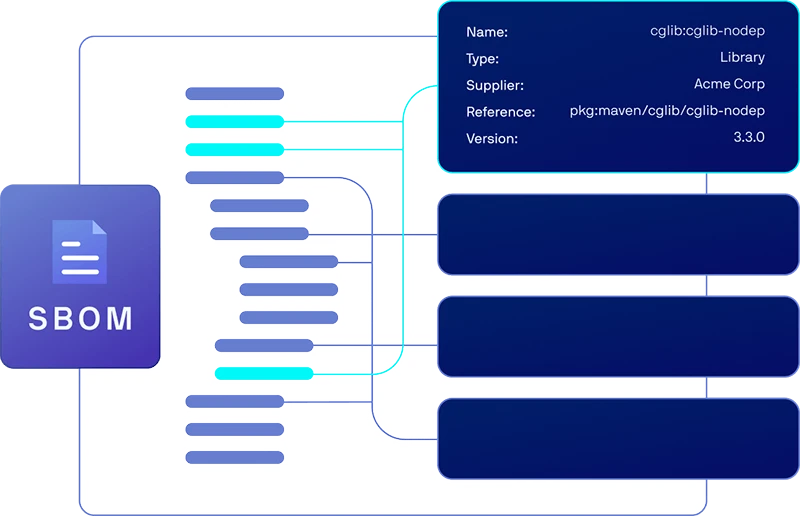
Continuously manage your software supply chain
- Maintain a continuous software bill of materials (SBOM) for declared and indirect third-party and open-source code packages.
- Manage SBOM data intuitively and share sensitive application information securely with customers and partners.
- Comply with requirements such as US Executive Order 14028.
- Identify overly restrictive open-source licenses that pose IP and financial risks.
Gain continuous coverage from code to run
- Automatically detect vulnerabilities within IDEs as developers write code.
- Continuously monitor code repositories for third-party dependencies and vulnerabilities.
- Check container images at build time using a plug-and-play inline scanner that integrates with CI or developer tools.
- Continuously scan applications in runtime for vulnerable packages, language libraries, and anomalous activity.
Features:
Third-Party Software Is Not Risk-Free
Visibility is no easy task
Organizations struggle to see indirect open-source or third-party dependencies and their associated vulnerabilities, creating blind spots in security.
Teams are overwhelmed
With limited visibility into indirect dependencies, teams face a constant flood of vulnerabilities and struggle to prioritize remediation.
There’s risk in the fine print
Companies face compliance and financial risk without a simple way to identify overly restrictive open-source license requirements.
Third-Party Code Without the Risk
List all your software components
Gain continuous visibility of third-party and open-source dependencies within your application.
Know where to focus first
Prioritize critical vulnerabilities based on how each vulnerable package is used within your application.
Shift left, not shove left
Secure code quickly and easily without slowing developers or requiring them to become security experts.
